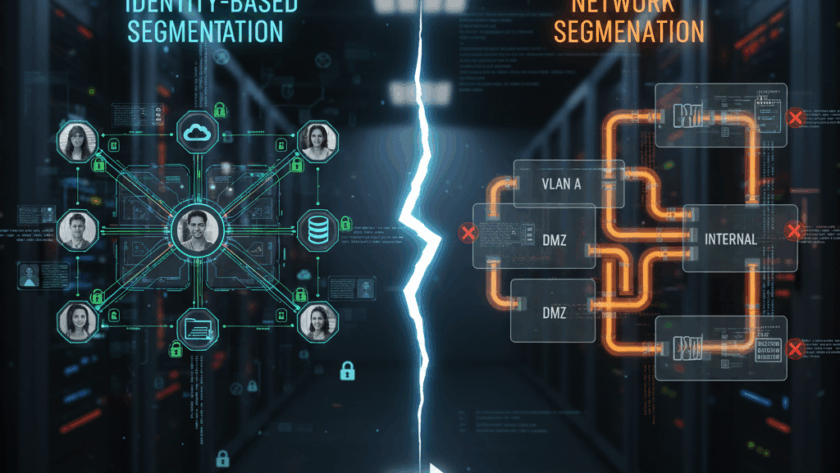
For years, enterprises relied on traditional network segmentation - VLANs, firewalls, and subnets - to separate critical resources from general traffic. It worked well in a static, on-premise world where…


Chat: AI Chat is not available - token for access to the API for text generation is not specified