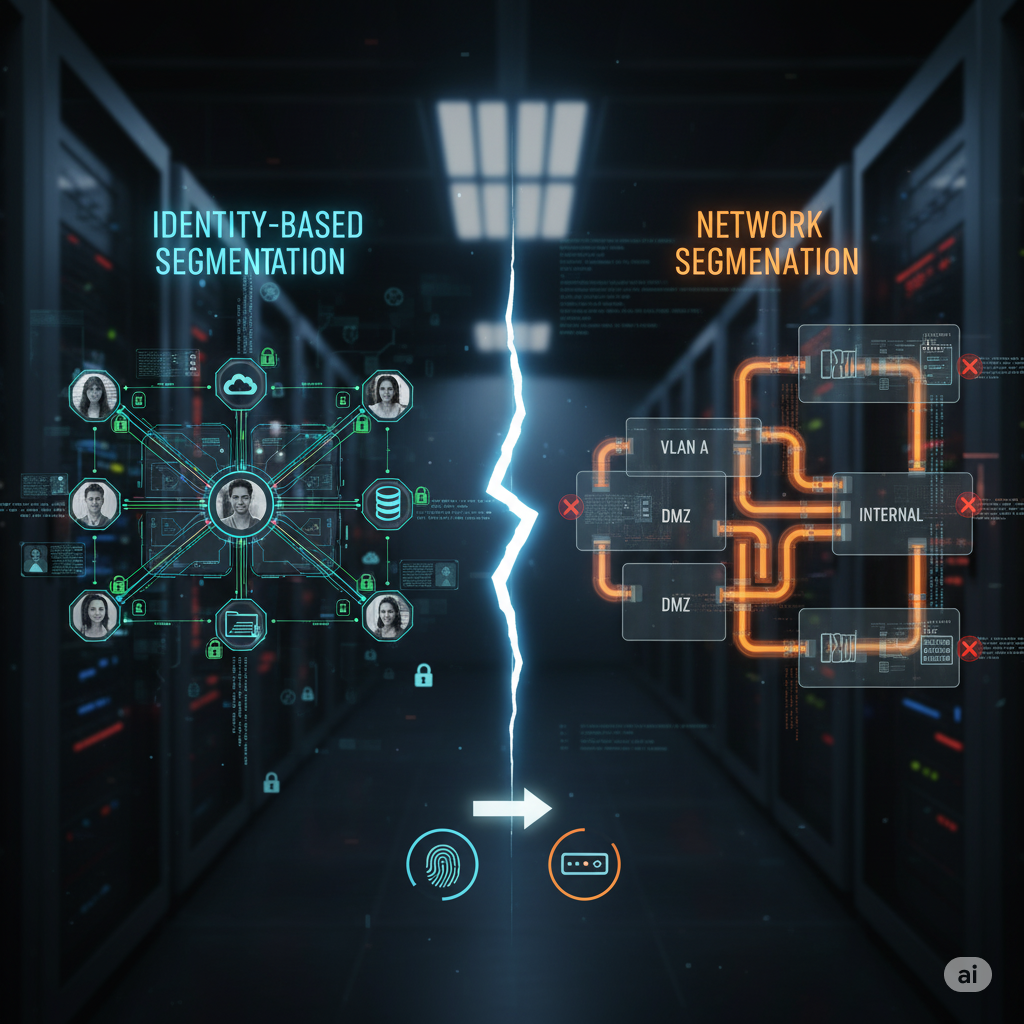
For years, enterprises relied on traditional network segmentation – VLANs, firewalls, and subnets – to separate critical resources from general traffic. It worked well in a static, on-premise world where applications stayed in one place and IP addresses rarely changed.
Fast-forward to the cloud era: workloads spin up and down in seconds, applications stretch across AWS, Azure, and GCP, and containers in Kubernetes clusters generate thousands of ephemeral IPs every hour. The old model simply cannot keep up.
This is where identity-based segmentation comes in. Instead of policies bound to where something is on the network, access rules are bound to what it is: a user, a workload, or a device. This identity-centric approach adapts fluidly to dynamic environments and aligns directly with Zero Trust microsegmentation principles.
In this article, we’ll explore the differences between network and identity-based segmentation, their respective strengths and weaknesses, and why identity-based segmentation is increasingly becoming the default strategy for securing hybrid and multi-cloud infrastructures.
Understanding the Basics
Network Segmentation
Network segmentation breaks a large network into smaller segments using tools like subnets, VLANs, ACLs, and perimeter firewalls. Each segment acts like a walled garden where rules can restrict inbound and outbound flows.
Benefits:
- Reduces broadcast domains and improves performance.
- Creates clear boundaries (e.g., PCI zone vs. corporate LAN).
- Well-understood by IT teams.
Drawbacks:
- Rigid and hard to scale across clouds.
- Requires network re-architecture for every major change.
- Blind to application identity or context.
Identity-Based Segmentation
Identity-based segmentation defines policies based on workload attributes or user identity. For example: “Payroll app can talk to Payroll DB, nothing else.” Instead of IPs, the system looks at labels like env=prod, app=checkout, or user=HR_admin.
Benefits:
- Policies follow workloads wherever they go.
- Granular controls prevent lateral movement.
- Strong alignment with Zero Trust.
Drawbacks:
- Requires consistent labeling and IAM integration.
- Higher upfront design effort.
- Needs modern platforms (agents, cloud-native tools, service mesh).
Comparison Table
Feature | Network Segmentation | Identity-Based Segmentation |
Policy basis | Subnets, VLANs, ACLs | Workload or user identity |
Granularity | Broad zones | Per workload, per user |
Flexibility | Static | Dynamic, cloud-ready |
Visibility | Network flows | Application & user context |
Zero Trust alignment | Indirect | Direct, least privilege |
NIST SP 800-207
The U.S. National Institute of Standards and Technology’s publication NIST SP 800-207 is the cornerstone of Zero Trust guidance. It defines Zero Trust as an architecture where no network location is inherently trusted. Every access request must be continuously verified, with least privilege enforced.
Within this framework, microsegmentation is a key control. NIST explicitly highlights segmentation based on identity – not network placement – as the way to enforce Zero Trust. This makes identity-based segmentation the natural successor to network segmentation.
Where traditional segmentation says “inside the perimeter is safe,” NIST insists there is no “inside.” Identities – users, devices, workloads – become the new perimeter. Access is granted or denied dynamically, based on policy, context, and risk.
By aligning with NIST’s Zero Trust model, organizations reduce reliance on static boundaries and embrace an identity-driven security posture.
Architecture of Microsegmentation
The Architecture of Microsegmentation provides the blueprint for applying fine-grained controls across modern IT environments. It typically includes:
- Network-based enforcement: using SDN overlays, firewalls, or switches.
- Identity-based enforcement: rules tied to workload labels, tags, or user groups.
- Cloud-native enforcement: AWS Security Groups, Azure NSGs, GCP firewalls.
- Service mesh enforcement: mTLS and sidecar proxies in Kubernetes clusters.
Each layer plays a role. Network segmentation still matters for broad isolation (e.g., separating production from dev). But the real power lies in identity-based segmentation, which controls east-west traffic at the workload or user level.
This architecture creates layered defenses: macro-segmentation from network rules, microsegmentation from identity-driven policies. Combined, they deliver resilience against modern threats.
Unlike traditional segmentation, which relies on static IPs, identity-based policies follow workloads wherever they run. This is especially important once you understand what is a cloud workload, since workloads today can be virtual machines, containers, or serverless functions that change dynamically across environments.
Agent-Based Microsegmentation
One of the most practical ways to implement identity-based policies is through Agent-Based Microsegmentation.
In this model, lightweight agents are deployed directly on workloads (VMs, containers, endpoints). These agents:
- Observe traffic flows and provide deep visibility.
- Apply deny-by-default rules locally.
- Enforce identity-driven policies.
- Report telemetry to a central policy controller.
Advantages:
- Granular control down to the process level.
- Policies follow workloads across clouds.
- Strong integration with IAM and orchestration tools.
Challenges:
- Agents must be deployed and maintained.
- May add performance overhead if poorly optimized.
- Requires coordination with DevOps teams.
Despite the challenges, agent-based models are widely adopted because they bring context-awareness to environments where IP-based rules fail – like containers and serverless workloads.
Comparative Analysis – Identity vs. Network
Network segmentation works best for static, predictable environments. Identity-based segmentation shines in dynamic, distributed ones.
Table: Identity-Based vs. Network Segmentation
Dimension | Network Segmentation | Identity-Based Segmentation |
Policy definition | IPs, VLANs, ACLs | User/device/workload identity |
Granularity | Coarse zones | Fine-grained per workload |
Cloud readiness | Limited | Native (labels, tags, IAM roles) |
Agility | Static, manual | Dynamic, automated |
Visibility | Packet-level | App-level, user-level |
Zero Trust alignment | Partial | Direct (least privilege, continuous auth) |
Best fit | Legacy data centers | Hybrid cloud, Kubernetes, Zero Trust programs |
Summary:
- Keep network segmentation for high-level isolation.
- Use identity-based segmentation for workload-level security and Zero Trust compliance.
Use Cases & When to Choose What
- Network Segmentation Use Cases:
- Legacy data centers needing compliance zones (e.g., PCI).
- Performance optimization by reducing broadcast traffic.
- Clear boundaries for IT teams already trained on VLANs and firewalls.
- Legacy data centers needing compliance zones (e.g., PCI).
- Identity-Based Segmentation Use Cases:
- Hybrid and multi-cloud environments.
- Kubernetes and containerized workloads.
- Protecting sensitive data workloads (finance, healthcare, IP).
- Enforcing Zero Trust in modern enterprises.
- Hybrid and multi-cloud environments.
- Combined Approach:
- Most enterprises blend both: network segmentation for macro-isolation, identity-based for microsegmentation.
Implementation Challenges and Pitfalls
While the benefits are clear, moving to identity-based segmentation isn’t simple:
- Labeling and identity hygiene: Policies are only as good as the labels and groups applied. Inconsistent labeling = broken security.
- Operational complexity: Deploying agents, managing policies, and monitoring telemetry requires cross-team collaboration.
- Cultural resistance: Network engineers are used to IPs and VLANs; shifting to identity-based thinking takes training.
- Policy sprawl: Without automation, rules can multiply quickly. Organizations need strong governance to avoid chaos.
- Tool sprawl: Many vendors offer overlapping features; integration is critical to avoid silos.
Mitigation strategies:
- Start small with a pilot (e.g., isolate one critical app).
- Automate policy creation using discovery tools.
- Integrate with existing IAM to leverage trusted identities.
- Phase rollout gradually instead of “big bang.”
Case Studies and Real-World Scenarios
Financial Services
A global bank needed to isolate its payment systems from general IT workloads. Traditional VLANs created too much complexity. By shifting to identity-based segmentation, the bank tied policies directly to applications and user roles. Result: faster compliance audits, reduced lateral movement, and simplified management.
Healthcare
A hospital group adopted agent-based microsegmentation for electronic health record (EHR) systems. Each workload had policies tied to identity attributes, not IP addresses. Even during ransomware outbreaks, attacks were contained within a single microsegment, protecting patient data.
Manufacturing
An industrial company with hybrid IT leveraged the architecture of microsegmentation: broad network zones for OT vs. IT, and fine-grained identity rules for workloads. This dual approach let them modernize securely without disrupting production.
These scenarios show that segmentation is not about “choosing one.” It’s about layering controls – network for macro, identity for micro – to deliver resilient security.
Conclusion
Both network segmentation and identity-based segmentation remain vital. The difference lies in their focus:
- Network segmentation secures based on where a resource lives.
- Identity-based segmentation secures based on what that resource is.
In today’s cloud and Zero Trust world, identity matters more. That’s why frameworks like NIST SP 800-207 emphasize identity-driven policies, why the architecture of microsegmentation puts identity at its core, and why agent-based microsegmentation has become the standard enforcement model.
The takeaway: don’t throw away network segmentation – use it for broad isolation. But layer identity-based segmentation on top to achieve the fine-grained, adaptive, and Zero Trust–aligned protection modern enterprises need.